Radio Equipment Directive (RED)
What is the Radio Equipment Directive (RED)?
The Radio Equipment Directive (RED) 2014/53/EU sets rules / Law for selling radio equipment in the EU.
It aims to create a single market by ensuring:
- Equipment is safe for users. – Health and Safety.
- Devices shouldn't interfere with each other - Electromagnetic Compatibility.
- Equipment must use radio frequencies effectively - Efficient Use of Radio Spectrum.
Additionally, it covers:
- Safeguards against fraud in order to protect personal data - Cybersecurity and Data Protection.
- Ensures radio-connected devices can work together - Interoperability.
- Guarantees access to emergency services - Emergency Services Access.
- Ensures compatibility between radio equipment and software - Software Compliance.
What devices are covered by the RED
The Directive covers all radio-enabled devices that actively initiate data exchange with the internet, including via Wi-Fi, LTE, 5G, Bluetooth and GPS.
Examples of equipment covered by the Directive are:
- Wi-Fi equipment (Anything with Wi-Fi including Printers, Projectors etc.)
- Bluetooth equipment (Anything with Bluetooth)
- Televisions
- Radio sets
- Mobile phones
- Satellite systems
- GPS systems
- Walkie Talkies
- Radar equipment
- etc.
When does the RED Delegated Act on Cyber Security start?
RED Cyber Security conformity requirements start on the 1st August 2025 in countries that require the CE mark (EU, UK & EFTA countries).
The law applies to any products placed on these markets after 1st August 2025. ‘Placed on the Market’ refers to when a product has entered the region and cleared customs.
In advance of this, Epson has been updating its product and compliant products started entering the market in June, 2025.
Why do we need RED Cybersecurity Requirements?
In today’s digital world, people increasingly rely on internet-connected devices for everyday activities such as online shopping, banking, and streaming. While this brings convenience, it also opens the door to cybersecurity risks, including unauthorised access to personal data, financial fraud and identity theft.
To address these growing threats, governments have introduced new cybersecurity requirements under the Radio Equipment Directive (RED) and regulations like the PSTI and the upcoming Cyber Resilience Act. These aim to ensure that connected devices are secure by design, meaning manufacturers must build in cybersecurity protections from the start.
Why does the RED Cyber Security Requirement matter?
The Radio Equipment Directive (RED) is the EU’s updated framework to ensure that all wireless and internet-connected devices meet strict cybersecurity standards before they can be sold on the European, UK and EFTA markets.
Manufacturers must comply with the new RED cybersecurity requirements.
These cover:
- Network integrity: Devices must not harm or misuse network resources.
- Data privacy: Devices must protect users' personal data.
- Fraud prevention: Devices must include safeguards against fraudulent activity.
Why it matters for Manufacturers
- Legal Compliance: Only RED-compliant products can carry the CE mark, which is required to sell in the EU, UK and EFTA markets.
- Penalties: Non-compliance can result in hefty fines and product withdrawal from the market.
- Market Access: Without RED compliance, manufacturers risk losing access to the EU, UK and EFTA markets entirely.
- The responsibility lies with the manufacturer, not the end user.
- While end users may choose to disable certain RED configurations (e.g., for legacy systems compatibility reasons), manufacturers must provide products that are RED-compliant.
What does this mean for users?
A key benefit of the RED configurations is improved Privacy and Data Protection intended to safeguard against fraud and protect personal data.
To achieve this, manufacturers are required to build in the product security safeguards. This includes encrypting the data being sent from one device to another, which makes personal information unreadable to unauthorized parties.
The data is encrypted at sending and de-crypted at receiving.
What is meant by Encryption and Decryption?
Encryption is a way of scrambling data so that only authorised parties can understand the information. It is the process of converting human-readable plain text into incomprehensible text, also known as ciphertext (ciphertext is a system of letters, numbers, or symbols).
Decryption is the process of converting encrypted data back into its original, readable form, or back into a form that you can understand and use normally.
RED Device Setup Workflow
The Radio Equipment Directive on Cyber Security came into effect on the 1st August 2025.
This means all RED compliant devices have their security functions enabled, and information transferred must be encrypted.
|
|
|---|
|
Before starting, please ensure you have administrative access rights for the device, as that is required to make changes to the system. If required, the security password can be found on a label on/in the device. |
Can you enable legacy protocols that RED compliance settings don’t support?
Yes, the customer has the right to choose whether RED compliance settings are maintained or to reconfigure machines back to non-RED compliance settings.
Whilst we do not recommend disabling the RED compliance settings (due to reduced security measures provided under the RED compliance settings), we understand that some customers may encounter interoperability issues while operation under RED compliance settings, for example if their systems cannot support them. If this is the case, the user may choose to manually enable port 9100 and LPR to connect to legacy network settings.
During this process, the system will alert the user to the risk of disabling the RED compliance settings by choosing to connect to the legacy network settings.
Should you choose to re-install legacy network settings and therefore disable the RED compliance settings, this will be at your own discretion and risk.
Please refer to the Epson support site for further support.
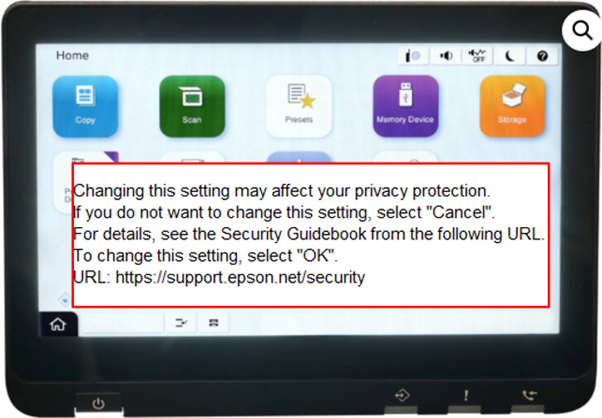
PLEASE NOTE: This workflow is based on EPSON’s WorkForce product range so images and menu options may vary.
To Start - Power on Printer

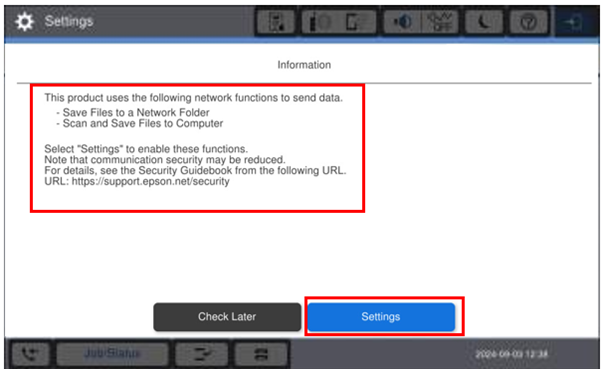
When a product is turned on for the first time the user will see the following message relating to the ‘file saving’ options:
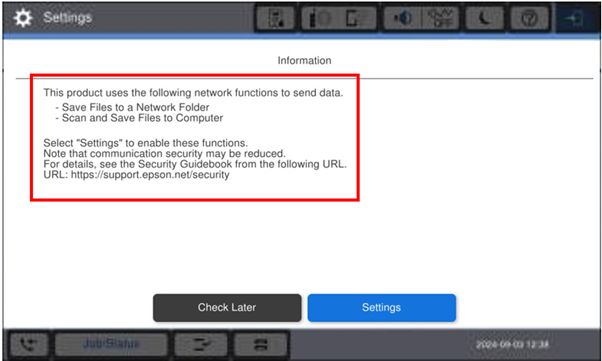
The user will have 2 options.
- Check Later
- Settings
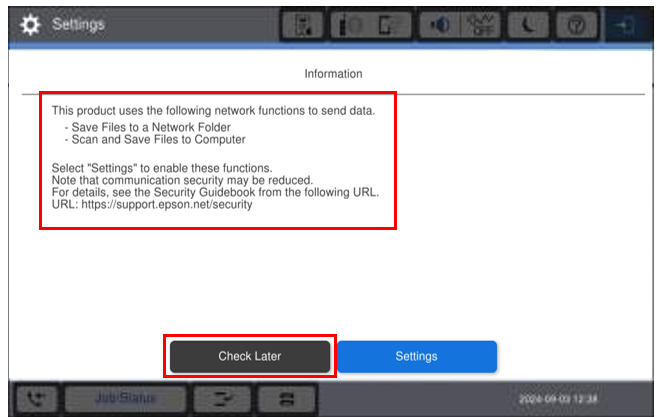
Option 1 - CHECK LATER
If you select “
Check Later” the default RED security setting will apply.
You will see a confirmation screen (Pictured below), Select
OK
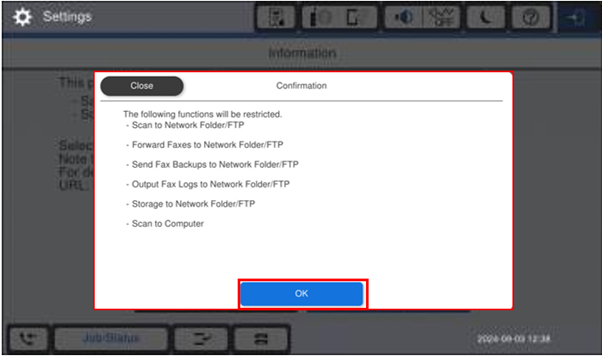
Option 2 - SETTINGS
If you want to “allow” the save file options, you may need to select the “Settings” option to disable selected RED features.
|
|
|---|
Read the message above carefully |
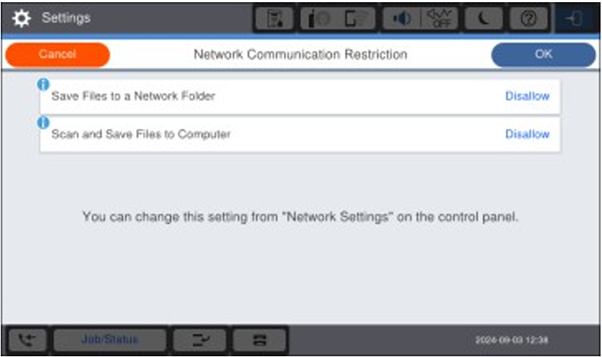
Enabling Save Options – Settings Selected
- As all security functions are enabled (by default), a user WILL NOT be able to save files to specific locations.
-
As you can see on the screenshot below, saving files to specified locations is “Disallowed”.
-
To enable a user to save files to specific locations, you may need to select “Allow” these functions.
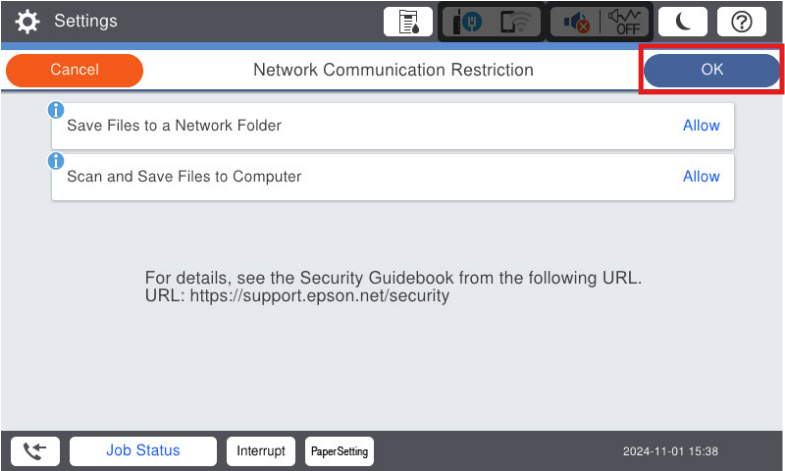
 IMPORTANT NOTE:
IMPORTANT NOTE:
If you enable these functions the communication security may be reduced.
For further details please see the Security Guidebook which can be found at
https://support.epson.net/security -
Click on
OK once you have made your selection.
-
Once you have completed the selection, the "Information" screen (pictured below) will no longer be displayed on startup.
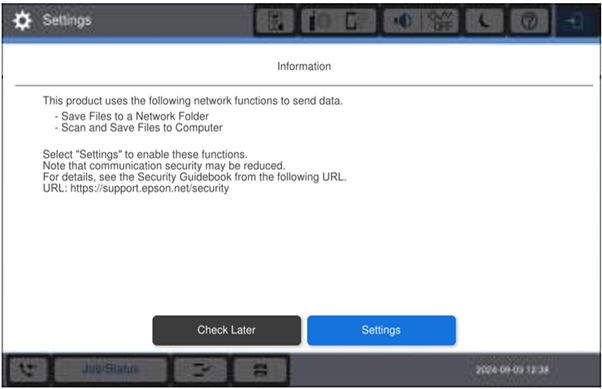
- After Restarting the device, it will go to straight to the home screen.
-
Start-up / Power on screen

-
Standard Home Screen
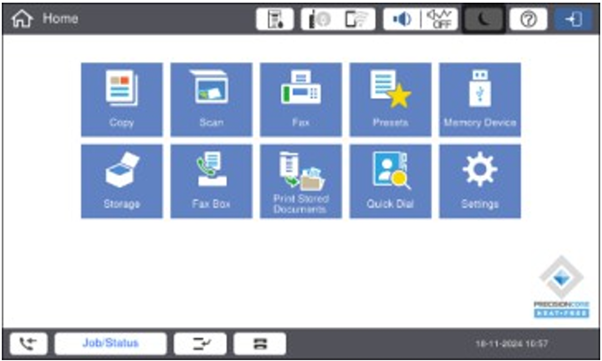
Check Later Selected
If a user selects “Check Later” on the initial startup, the RED security settings will be ON / ENABLED.
If a user wishes to disable the RED settings and enable the “Save to” options, then the recommended method to enable this is through the panel / screen on the device.
-
Start by selecting the “Settings” option on the panel
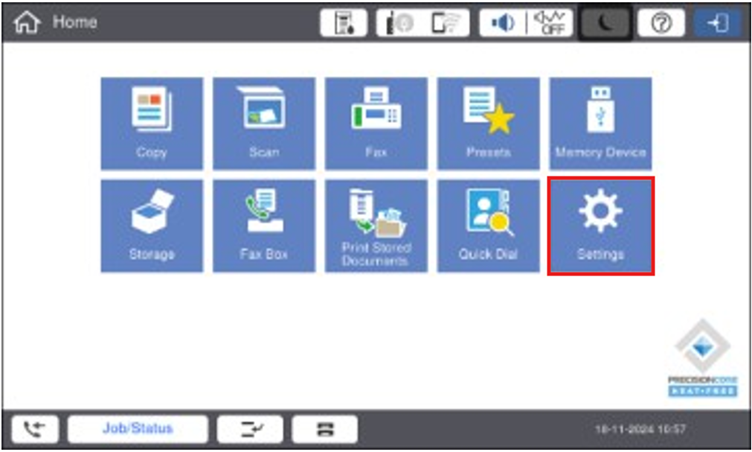
-
The user will then see the information screen, Select Settings. Read the message below carefully!

-
The user will then see an information screen, explaining what can be enabled. Click on OK
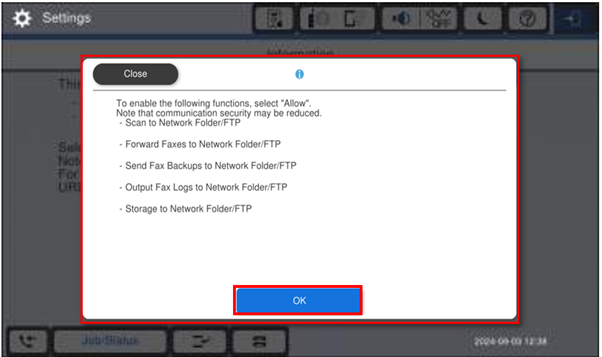
A second information screen is shown. Click on OK
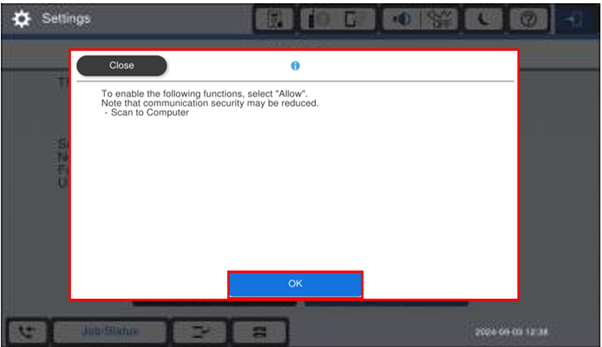
-
Select Network Settings
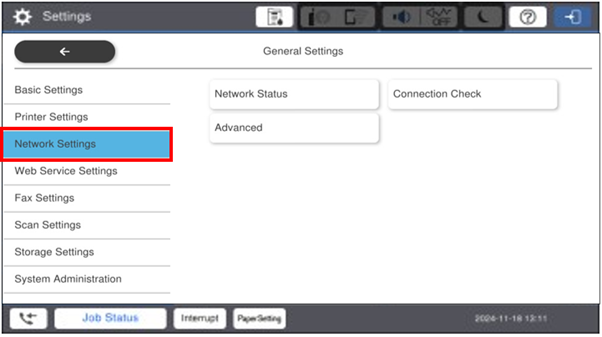
-
Then select Advanced
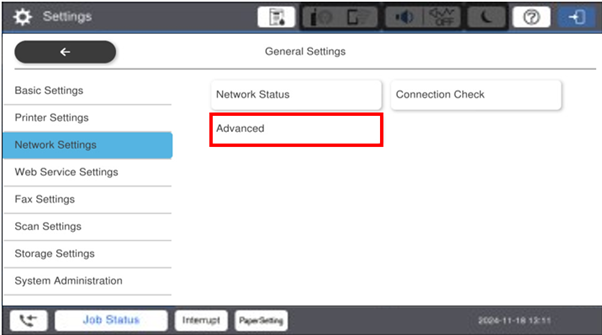
-
After the Advance selection you should see a confirmation screen with the security warning message. If you wish to proceed, click OK.
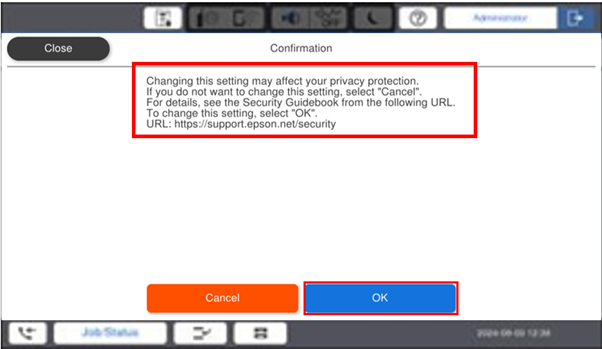
-
Select Network Communication Restriction
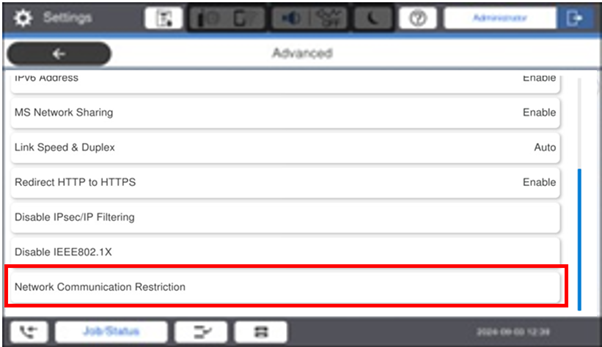
-
Select “Allow” the save options that are required and then click on OK.

Once you have completed the selection, the "Information" screen below will no longer be displayed.

You will be returned to the “Home” screen, and the setup is complete.

You should now be able to save files to the computer and any specified Network folder.
Other Options - Legacy Modes
Note that each time you enable “Legacy mode”, communication security is reduced.
What can a user do to get things working again?
-
If compatibility with an existing printing environment is compromised:
- Install a printer driver/application that supports RED configurations
- OR
-
You may enable “Legacy mode" using the following methods
- Web Config
- Epson Device Admin
-
If printing performance is reduced:
-
You may enable “Legacy mode" using the following methods
- Web Config
- Epson Device Admin
- Re-configure Epson proprietary port or re-install printer driver/application
-
You may enable “Legacy mode" using the following methods
How to Enable “Legacy mode” in Web Config
Tick the following three items
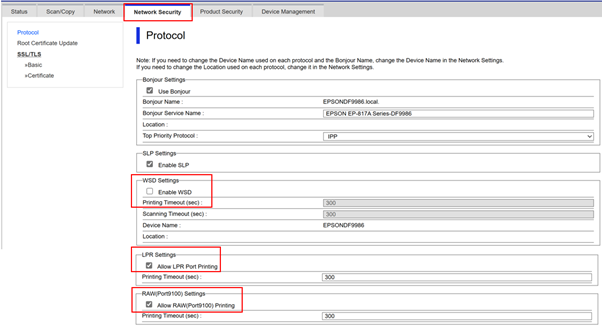
How to Enable “Legacy mode” Epson Device Admin
Connect to Web Config and tick the following three items within the network.
- WSD settings: Enable WSD.
Port management:
- (1) Allow printing from the LPR port.
- (2) Allow printing from RAW (Port 9100).
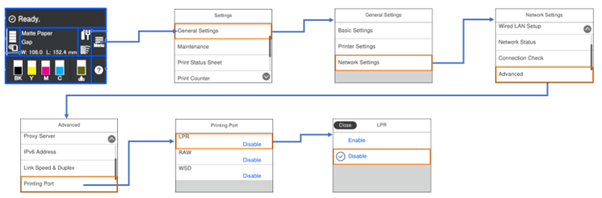
How to Enable “Legacy mode” on the device panel
In the Network settings select:
- LPR
- RAW
- WSD
Factory Default
If in doubt, reset to Factory Defaults
If at any time you are not sure what has and has not been changed, the easiest option is to reset the device back to factory defaults.
With a RED cybersecurity compliant product this means that the device will reset back to RED security compliant settings.